Hot on the tail of our recent article on new Android malware discovered by Palo Alto Networks (and the scary numbers released by Bitdefender), ESET has identified that a new trojan named Android/Spy.Agent.SI is mimicking banking and other financial applications on Android devices.
According to media releases, millions of customers of Australia and New Zealand’s largest banks may be targeted.
Discovered January 29 2016, the trojan is also known as HEUR:Trojan-Banker.AndroidOS.Agent.au (Kaspersky) and Android.SmsBot.539.origin (Dr.Web).
The malware presents victims with a fake version of the login screen of their banking application and locks the screen until they enter their username and password. Using the stolen credentials, the thieves can then log in to the victim’s account remotely and transfer money out.
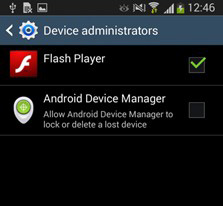 They can even get the malware to send them all of the SMS text messages received by the infected device, and remove these. “This allows SMS-based two-factor authentication of fraudulent transactions to be bypassed, without raising the suspicions of the device’s owner,” explains Lukáš Štefanko, ESET Malware Researcher who specialises in Android malware.
They can even get the malware to send them all of the SMS text messages received by the infected device, and remove these. “This allows SMS-based two-factor authentication of fraudulent transactions to be bypassed, without raising the suspicions of the device’s owner,” explains Lukáš Štefanko, ESET Malware Researcher who specialises in Android malware.
In its current state, the Trojan spreads as an imitation of Flash Player application. After being downloaded and installed, the app requests administrator rights to protect itself from being easily uninstalled from the device. It then checks if any target banking applications are installed on the device, and if they do, it downloads fake login screens for each banking app from its command and control server. When the victim launches a banking app, a fake login screen appears over the top of the legitimate app, leaving the screen locked until the victim submits their banking credentials.
It currently targets major banks in Australia, New Zealand and Turkey. In fact, the 20 financial institutions currently targeted by the app include the largest retail banks in each of the three countries. Examples of the fake overlays are:
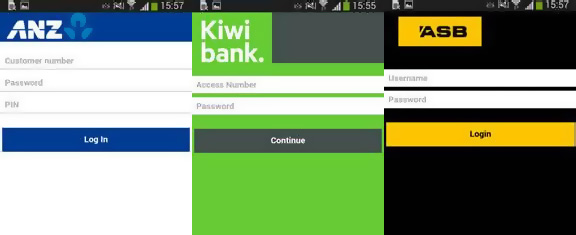
The full list of targeted banks include: ANZ Bank, Commonwealth Bank, National Australia Bank, Westpac, St. George Bank, Bendigo Bank, Bankwest, Me Bank, ASB Bank, Bank of New Zealand, Kiwibank, Wells Fargo, Finansbank, Halkbank, VakfBank, Garanti Bank, Yap Kredi Bank, Akbank, Türkiye Bankas and Ziraat Bankas.
“The attack has been massive and it can be easily re-focused to any another set of target banks,” warns Lukáš Štefanko.
Hackers can make millions if they get the malware model right, as we saw with cryptolocker. Successes like cryptolocker mean there will always be people and organised groups trying to develop new ways to exploit devices and systems. Fortunately, there are things you can do to protect yourself.
- If you see anything masquerading as Adobe Flash Player on Android, you can be sure it’s fake. Flash Player hasn’t created a client for Android since 2012, so it is highly unlikely anything legitimate is still making the rounds on the mobile platform.
- Only install mobile apps from the official Google Play Store rather than third-party sites.
- Add antivirus to your devices. This will only detect known threats, but may pick up something you miss.
Last but not least, if you do become infected with Android/Spy.Agent.SI, you can remove the malware by disabling the fake Flash Player’s administrator privileges in Settings or by removing it while in Safe Mode.
As always, we encourage all clients to add employee training on spotting potential security threats to their training programs. While this trojan targets banking applications, it could easily be modified to target business applications or services, presenting an entirely different array of issues for organisations.
For more information on security, or educating your staff on how to identify malware before it becomes an issue, contact the blueAPACHE account team.

