Another phishing attack, but with a local financial entity and a real Inuit email address.
As we have mentioned in previous blog entries, it is often easy to identify the less mature malware attacks by simply checking the email addresses or holding you mouse over any links to show their true destination.
Today, we received notification of emails that present as invoices from Sequoia Financial Group; a legitimate financial services company in Melbourne and Sydney.
The email appears genuine, seemingly sent from the popular Intuit Quickbooks accounting software. The sender address is [email protected], appearing exactly as would expect for an online invoice notification. None of the normal fake email tell tale signs were present – this looked for all intents and purposes to be correct. Except it isn’t.
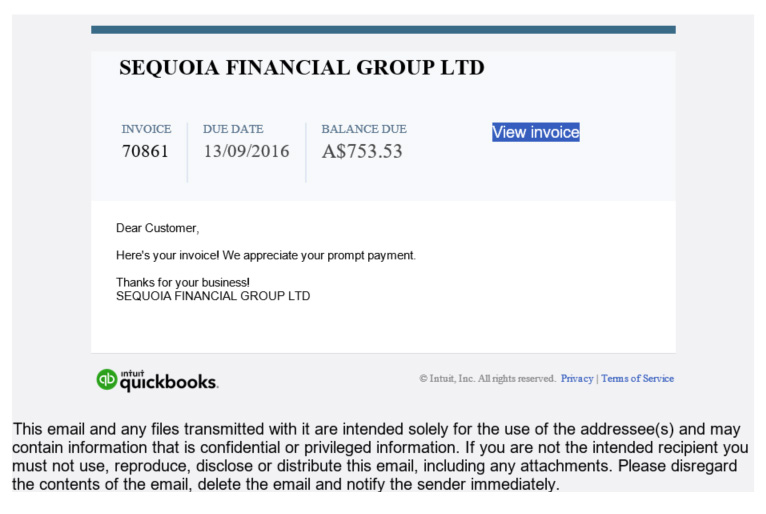
The problem is the view invoice link. The link is difficult to read when hovering your mouse over, as it is automatically generated through a popular mail management program. Clicking to access the invoice will automatically download a file entitled Invoice_70861.zip. The file inside the downloaded zip file is Invoice_70861.js.
If you open this file to read the invoice, the trojan is installed and no file is displayed.
The trojan then accesses the Kernel Security Device Driver (KsecDD) of Windows, reads personal information, creates writeable files in a temporary directory, writes PE32 executable console files to disk, creates mutants, reads Windows trust settings and system certificate settings, connects to LPC ports, enters URL in binary, connects to two domains (USA and UK based IP address), and contacts 6 hosts located in Germany, Russia and United Kingdom. At this point, you may well have lost control of your computer.
John Collignon, Sequoia Financial Group’s Head of Superannuation, stated that the company “is aware of the emails and that someone is pretending to be us”. He confirmed that Sequoia had received reports today of emails masquerading as Xero and Quickbooks invoices, and explained he was not aware why the company brand was being maliciously used by hackers to distribute malware.
Sequoia are not the only company being targeted in the bulk email campaigns trying to distribute Invoice_70861.js. Our security systems are blocking thousands of these emails each day. Not all share the levels of detail as seen in the Sequoia email, which makes it stand out.

Any company can be targeted by hackers looking to benefit from your reputable brand to encourage individuals to unwittingly install trojans or malware. This attack using Sequoia’s brand reinforces:
- Australian businesses are not immune to being targeted. We need mature levels of awareness, process and security to manage the risk.
- Security is becoming the key focus for IT departments around the world,. Failure to secure your data can have far reaching ramifications.
- Quality training to educate staff, customers and suppliers on how to spot phishing emails and social engineering attacks should be high on your education priorities.
- If you receive an email you are unsure of, phone the company directly to validate it before clicking any links.
Note
blueAPACHE explicitly agrees that Sequoia Financial Group is in no way responsible for the distribution of Invoice_70861.js. We suspect their brand was likely hijacked by an unknown party to invoke higher levels of confidence in the email, in hope that more recipients would access the invoice and unknowingly install the trojan software.
For more information on how to better secure your business, contact the blueAPACHE account team.

