The past few weeks haven’t been great for Lenovo, and rightly so. Security researchers recently discovered that consumer-grade Lenovo computers ship with software called Superfish Visual Discovery that injects advertising (using web-intercepting technology from Komodia) into websites as you’re viewing them.
This software was pre-installed on new computers by Lenovo since at least mid-2014 as crapware (also known as bloatware, adware or junkware). While this is normally a small annoying piece of software that people uninstall, Superfish has the potential to hijack SSL and TLS connections – a severe, nasty security vulnerability.
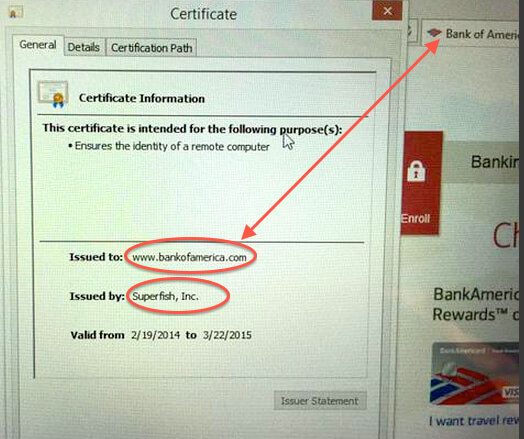
To extend the capability of injecting advertising across secure sites, Superfish also installed a self-generated root certificate into the Windows certificate store and then resigned all SSL certificates presented by HTTPS sites with its own certificate – the classic definition of a man-in-the-middle attack. It’s a weakness that hackers could potentially use to steal sensitive data like banking credentials and capturing your web surfing activities.
According to Chrome security engineer Chris Palmer, Superfish appears to be using the same root certificate with the same weak RSA key on all affected Lenovo PCs, rather than generating unique encryption for each computer. A hacker could, for example, create a single phony banking site relying on the faked Superfish security certificates for authentication. Under this scenario, all affected Lenovo PCs would not be able to detect they were visiting a forged site.
Facebook’s own Threat Infrastructure team said that while it is not uncommon for PC products to come pre-loaded with applications, Superfish is different due to its ability to intercept SSL and TLS website connections. Superfish is able to inspect this content, and uses a third-party library from Komodia to “modify the Windows networking stack and install a new root Certificate Authority (CA),” which in turn gave the adware power to impersonate any SSL-enabled website. “The new root CA undermines the security of web browsers and operating systems, putting people at greater risk,” Facebook’s team says.
Social backlash
As this fiasco has come to light in recent weeks, Lenovo has suffered huge social backlash with individuals and organisations claiming they would never purchase from Lenovo again.
A week after it hit the press, the Lizard Squad hacking group took complete control of the company’s valuable Lenovo.com domain name, a coup that allowed them to intercept all company email and impersonate its web pages. People who visited the site during the attack saw a slide show that when clicked, led to a Twitter account that sharply criticised Lenovo.
We expect Lenovo to aggressively pursue the Lizard Squad and seek prosecution to deflect attention and position themselves as victims, which is a little hypocritical.
The business case
Superfish paid Lenovo for the privilege of having their software pre-installed on new Lenovo PCs. According to sources with knowledge of the deal, Lenovo certainly made less than $500,000 from Superfish. Forbes believes the deal was only worth between $200,000 and $250,000, a paltry sum given the potential legal and PR costs the company has and will incur. Individuals have already started legal action against Lenovo, with discussion of a class action gathering force.
The result
This week, Lenovo released a statement claiming they would eradicate crapware from all machines in future. “We are starting immediately, and by the time we launch our Windows 10 products, our standard image will only include the operating system and related software, software required to make hardware work well (for example, when we include unique hardware in our devices, like a 3D camera), security software and Lenovo applications,” the company said in a statement.
Additionally, they published instructions on how to uninstall the software, which can be found at http://support.lenovo.com/us/en/product_security/superfish_uninstall