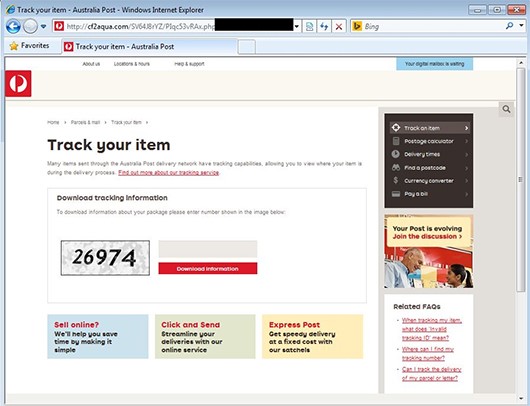
Another round of ransomware is targeting Australians. This new incarnation masquerades as an Australia Post email notifying you of a parcel and encouraging you to check tracking, which is similar to those floating around last year. Clicking the tracking link takes you to a site that looks like Australia Post, but is not.
It is very important that you avoid unexpected Australia Post emails, links contained on those emails and prompts to enter the captcha codes. Even if you are expecting a parcel, you need to be vigilant. We recommend you phone Australia Post on 13 76 78 to verify the email before opening.
Trend Micro report there are 17 fake websites used so far (the list is still growing). The URL for these include random addresses like hxxp://psyjukebox-mobile.com:80/GNt0IbcZhn/2zsNj4FphXidHK.php – so you should be able to quickly identify them as fake sites.
The malware used is TorrentLocker, a type of ransomware that encrypts all files on your network. There is no known way to unencrypt your data without paying ransom fees in these newer versions.
TorrentLocker infections are almost always initiated with a spam email. We’ve seen spam campaigns with the TorrentLocker executable directly attached to the email message, as well as some that have included an attached office document with an embedded macro that will download and execute the TorrentLocker file. Other campaigns have also been observed, including some that include a link which, if clicked on, redirects the victim to a download of the TorrentLocker file.
Once downloaded, TorrentLocker will usually attempt to delete volume shadow copies (to remove the chance of file recovery), copy itself to the windows directory and contact the command and control server. An encryption key is then generated and all accessible files on the network are encrypted.
Upon encryption, the ransom message is displayed and details of the encrypted files are sent to the command and control server. TorrentLocker then harvests email accounts from your email programs (including online email accounts) and sends them to the command and control server to further spread the malware.
As with most ransomware, payment is made with bitcoins and the instructions are accessed through Tor. TorrentLocker accepts a reduced fee if payment is made within a short period of time (usually four days), after which the price doubles. It is claimed that after one month the decryption key will be destroyed and encrypted files will be unrecoverable.
The decryption file is typically priced between $500 and $1000. Even when paying, there is no guarantee that you will receive the key to decrypt your files, or that the key will work.
If you have concerns about your security posture, or would like staff training on how to spot suspicious emails and sites, contact the blueAPACHE account team.

