The 2016 $US81m heist (which could have been much worse!)
In February 2016 during Chinese New Year, one of the most brazen and largest digital heists in history took place. A group of unidentified hackers used sophisticated malware to study bank workers and subsequently divert $US81 million from a Bangladesh Central Bank account at the Federal Reserve Bank of New York to multiple accounts in Sri Lanka and the Philippines.
The instructions to steal the funds were issued via SWIFT – the Society for Worldwide Interbank Financial Telecommunication – a highly trusted and ubiquitous network used by thousands of financial institutions worldwide to facilitate transfers between banks. Computer security researchers have linked this theft to as many as 11 other attacks worldwide, all executed using the SWIFT banking network.
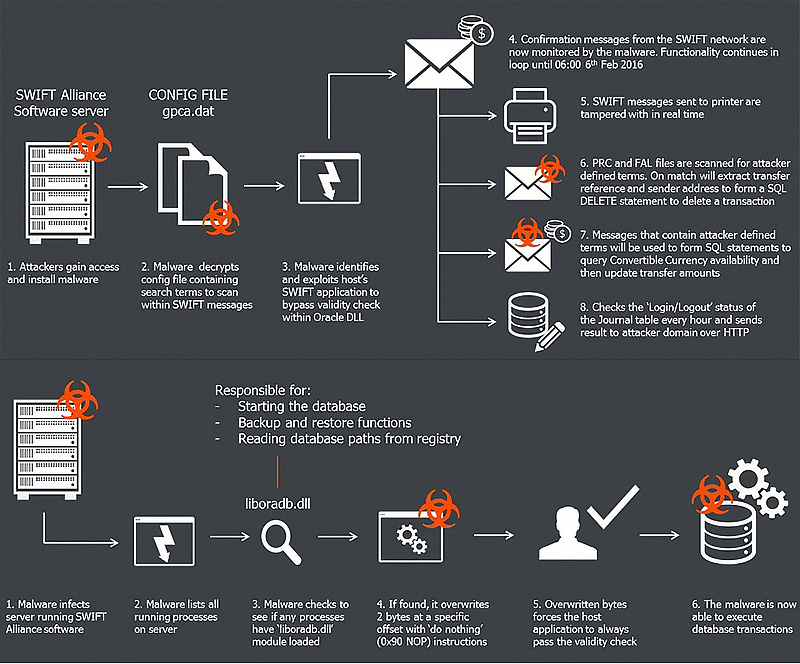
The attacks involved malware written to issue unauthorised SWIFT messages and to conceal that the messages had been sent. In some cases, access was gained through targeted social engineering attacks that encouraged employees to inadvertently disclose their credentials and private access information.
The hackers managed to compromise Bangladesh Bank’s system, observe how transfers are done, and gain access to the bank’s credentials for payment transfers, which they used to send requests to the Federal Reserve Bank of New York to transfer funds. 30 transactions worth $851 million were prevented by the banking system – but five requests were granted; totalling $20 million to Sri Lanka (later recovered) and $81 million lost to the Philippines.
According to reports, the core messaging system of SWIFT was not breached; instead, the criminals attacked the banks’ connections to the SWIFT network. Most banks have governance to identify fraudulent transactions, however the malware deletes evidence of the hackers’ activities and subverts normal business processes to remain undetected.
Implications
Hackers are increasingly focusing on SWIFT and other private platforms. Aside from the greater transactional values (and fewer alarms for high value transactions), SWIFT’s security is not equipped to deal with the progressively sophisticated attacks from modern day hackers. The 30 transactions that were prevented were typically halted through human intervention due to common spelling mistakes (“fundation” instead of “foundation” for example).
According to BAE Systems, a defence and security company that analysed the attack, “the general tools, techniques and procedures used in the attack may allow the gang to strike again. All financial institutions who run SWIFT Alliance Access and similar systems should be seriously reviewing their security now to make sure they too are not exposed.
“The wider lesson learned here may be that criminals are conducting more and more sophisticated attacks against victim organisations, particularly in the area of network intrusions.”
Moving forward
These attacks signal a warning not just for the SWIFT platform and financial institutions, but any organisation that deals with private platforms. Users of procurement, contract and payment gateways need to be cautious. Private platforms might feel safe, but as the value and awareness increases, targeted threats against specific organisations are becoming increasingly common and effective.
The way your network is structured can potentially open up your entire data infrastructure to threats. Dividing the network into segments or placing data in separate disconnected networks may minimise the impact of a targeted attack. Intelligent network architectures can contain attacks and minimise damage automatically, moving organisations away from a reactive solution.
The SWIFT hacking also serve as a grim reminder that cyber security is as much about people as it is about technology – with sophisticated hackers being been able to recruit employees to hand over credentials and other key details.
Cyber security awareness training is one of the most effective ways to prevent social engineering attacks. If employees know what to look out for, are vigilant, and question any suspicious information request, then they are less likely to become an unwitting accomplice to such attacks.
If you have concerns about the threats of potential cyber-attacks on your organisation, or would like staff training on security awareness, contact the blueAPACHE account team.