A recent presentation by the CEO of Microsoft, Satya Nadella, revealed the impact of hackers on the global business community. He illustrated that in 2015, cybercrime resulted in:
- More than 160 million customer records were compromised by the top eight reported breaches in 2015.
- Around $3 trillion of market value was destroyed. The lost productivity, lost growth and business impact caused by cybercrime led to the $3 trillion estimate.
He also highlighted that it was 229 days on average between infiltration and detection. The exploits were remaining undetected for well over 6 months on average, which highlights businesses’ lack of security audit and process. You may already be breached, and simply haven’t identified it yet.
This isn’t a new phenomenon as Nadella explained; “if you look at the history of computing or history of all information technology, starting from when we started to store data, transmit data and communicate, we’ve always had attacks on trust. With mail came mail fraud. With the telegraph, radio and television came wire fraud. And now with the Internet we have cybercrime.”
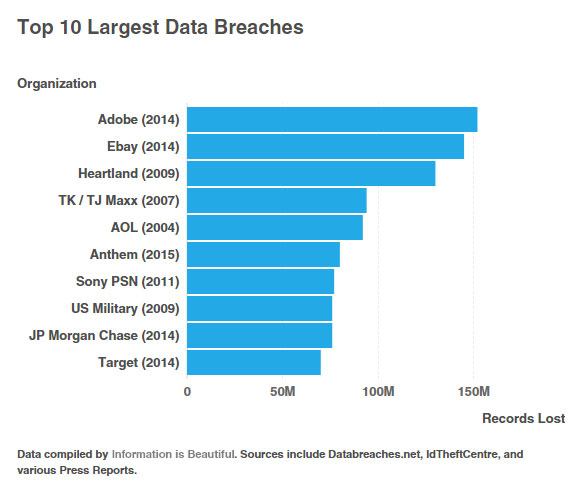
Technology has moved from our IT environment which we control, to be an extended global network. Security has not kept up with the changing nature of how business is done. Today however, like the speed of transactions, is that the speed of fraud and the damage done has increased exponentially. Microsoft saw more businesses suffering security breaches last year than ever before. They also saw more irretrievable destruction of data and more lost productivity amongst their clients than in any year previously.
Nadella continued “there isn’t any aspect of our life, how we entertain ourselves, how we do commerce, how we educate our boys and girls, there isn’t a part of the economy from retail to healthcare to energy that is not using digital technology today to drive innovation and transform itself. So it’s become the core of not just tech industry but the core of every industry. But customers are not going to use this technology if they can’t trust it”.
And here lies the technology key. Creating environments (whether they be cloud or on-premises) that deliver the security to meet regulatory privacy requirements and the continuity businesses demand, is no longer a ‘nice to have’ – it is essential. This is further amplified by the proposed Australian legislation demanding data breaches be reported by all businesses with revenue over $3 million. The impact a breach has when announced into the public domain presents a wrath of trust and technology challenges that some will struggle to overcome.
To better understand your security profile, contact the blueAPACHE Consulting Team.

